‘Starkiller’ Phishing Service Proxies Real Login Pages, MFA – Krebs on Security

Most phishing websites are little more than static copies of login pages from popular sites on the Internet, and are often quickly taken down by anti-bullying activists and security companies. But a new deceptive phishing offering allows customers to avoid both pitfalls: It uses hidden links to load the target product’s website, then acts as a relay between the target and the legitimate site — forwarding the victim’s username, password and multi-factor authentication (MFA) and returning the legitimate victim’s response code.
There are many phishing kits that would-be fraudsters can use to get started, but using them successfully requires some skill in configuring servers, domain names, certificates, proxy services, and other repetitive technical concerns. Come in Starkillera new phishing service that dynamically loads a live copy of a target’s login page and records everything the user does, intercepts the data on the legitimate site and returns it to the victim.
According to the analysis of Starkiller by the security company Weird AIthe service allows customers to choose a brand to impersonate (eg, Apple, Facebook, Google, Microsoft et. al.) and generate a spoofed URL that mimics a legitimate domain while routing traffic through the attacker’s infrastructure.
For example, a phishing link targeting Microsoft customers appears as “login.microsoft.com@[malicious/shortened URL here].” The “@” in link trick is an oldie but a goodie, because everything before the “@” in the URL is treated as username data, and the actual landing page is what comes after the “@” sign. Here’s how it looks in the target’s browser:
Image: Weird AI. The actual malicious landing page is blurred in this image, but we can see that it ends in .ru. The service also provides the ability to embed links from different URL shortening services.
When Starkiller clients select a URL to be spoofed, the service spins up a Docker container running a headless Chrome browser instance that loads the real login page, Odds Found.
“The container then acts as a proxy that distorts the middleman, relaying the user’s input to the legitimate site and returning the site’s responses,” Uncommon Researchers. Calli Baron again Piotr Wojtyla he wrote on his blog on Thursday. “All keystrokes, form submissions, and session tokens pass through attacker-controlled infrastructure and are logged along the way.”
Starkiller essentially offers hackers real-time session monitoring, allowing them to live-stream a target’s screen as they interact with a phishing page, the researchers said.
“The platform also includes keylogger capture of all keystrokes, cookie and session token theft for exact account takeover, geo-tracking of targets, and automatic Telegram alerts when new credentials come in,” they wrote. “Campaign analytics include user experience with visit statistics, conversion rates, and performance graphs—the same type of metrics in a formal SaaS dashboard [software-as-a-service] platform can provide. “
Strange said the service also captures and transmits the victim’s MFA credentials, as the recipient who clicks the link actually authenticates with the original site by proxy, and any authentication tokens sent are then transmitted to the legitimate service in real time.
“The attacker captures the resulting session cookies and tokens, giving them authenticated access to the account,” the researchers wrote. “When attackers bypass the entire authentication flow in real time, MFA protections can be effectively bypassed even though they are working as designed.”
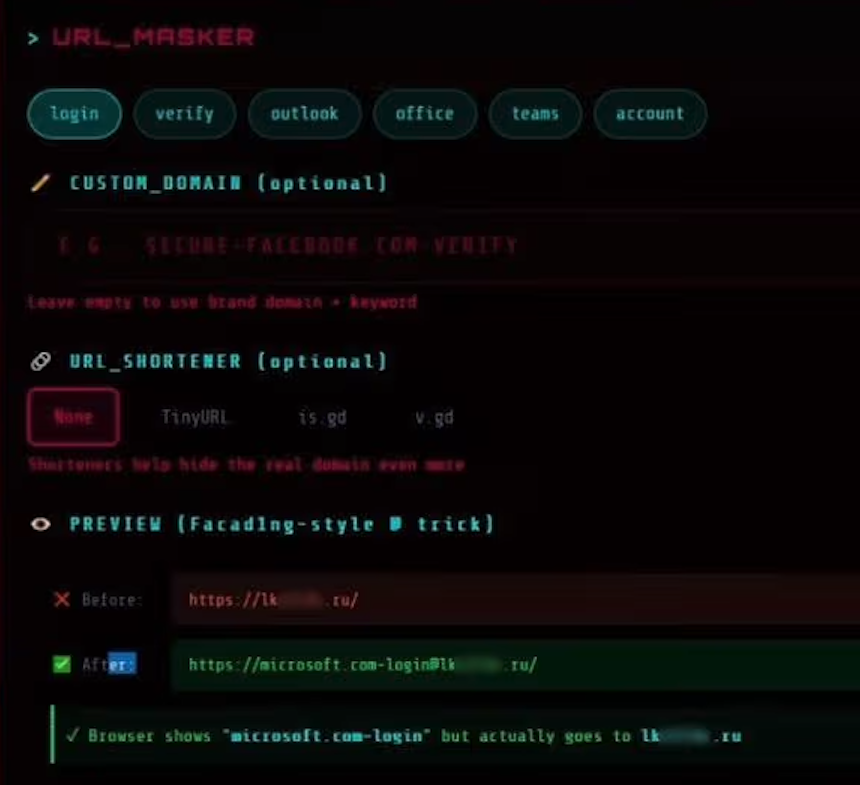
The “URL Masker” feature of the Starkiller phishing service includes malicious link blocking options. Photo: Unusual.
Starkiller is one of the few cyber crime services offered by a self-proclaimed threat group Jinkusuwhich maintains an active user forum where customers can discuss strategies, request features and troubleshoot issues. One a-la-carte feature will harvest email addresses and contact information from compromised sessions, and advises that the data can be used to build target lists for phishing campaigns.
This service strikes me as an amazing revolution in phishing, and its apparent success could be copied by other cybercriminals (assuming the service works as intended). After all, phishing users in this way avoid the upfront costs and ongoing hassles associated with aggregating multiple phishing domains, and it challenges traditional phishing detection methods such as domain indexing and static page analysis.
It also significantly lowers the barrier to entry for novice cybercriminals, Uncommon researchers note.
“Starkiller represents a significant growth in the phishing infrastructure, reflecting a broader trend towards the use of commercial and business-style cybercrime,” their report concluded. “Combined with URL obfuscation, session hijacking, and MFA bypass, it gives low-skilled hackers access to previously inaccessible attack capabilities.”




