Cybersecurity in 2026: AI Attacks, Identity‑First Defense, and the New Playbook for Resilience

Cybersecurity in 2026: AI Attacks, Identity‑First Defense, and the New Playbook for Resilience
Ransomware activity hit new highs, identity is the core attack surface, and AI is accelerating both sides. Here’s the data‑driven playbook for 2026—with a real‑world case study you can learn from.
- AI is everywhere—from personalized phishing and automated intrusion to faster detection and response on the blue team. Sources: Google Cloud, ISACA, Dark Reading.
- Identity is the new perimeter: stolen credentials and MFA gaps dominate incidents; adopt phishing‑resistant MFA, JIT admin, device trust. Sources: Mandiant M‑Trends 2025, ISACA.
- Resilience > prevention: measure time‑to‑detect/contain/recover; plan clean‑room recovery; vendor kill‑switches are a must. Sources: SecurityWeek Outlook 2026, IBM Cost of a Data Breach 2025.
1) AI Everywhere: Offense Scales, Defense Accelerates
Attackers are moving from sporadic AI usage to standardizing AI in their playbooks: hyper‑personalized phishing, automated reconnaissance,
and even early “agentic” orchestration that can plan and adapt during intrusions. On defense, AI‑assisted detection/response is cutting breach lifecycles and cost—IBM reports organizations
with security AI and automation save nearly $1.9M per breach on average.
Google Cloud Forecast 2026,
ISACA 2026 Trends,
IBM Cost of a Data Breach 2025.
What to do this quarter
- Govern AI usage: inventory LLM apps/agents; block “shadow AI” where needed; enforce access controls and logging. IBM 2025
- Red‑team your AI: add prompt‑injection tests and model abuse checks to your appsec program. Google Cloud

2) Identity Is the Core Attack Surface
Mandiant’s frontline data shows stolen credentials rose to the #2 initial access vector (16%), driven by infostealers and unmanaged endpoints; exploits remain #1 (33%).
Most modern intrusions leverage valid credentials, not just malware. That’s why phishing‑resistant MFA, strong device trust, and just‑in‑time admin are non‑negotiable in 2026.
Mandiant M‑Trends 2025,
ISACA.
Playbook upgrades
- Phishing‑resistant MFA (passkeys, security keys, platform biometrics) for employees, vendors, and admins.
- JIT privilege & session recording for break‑glass access.
- Device trust: block access from unmanaged/unhealthy devices.

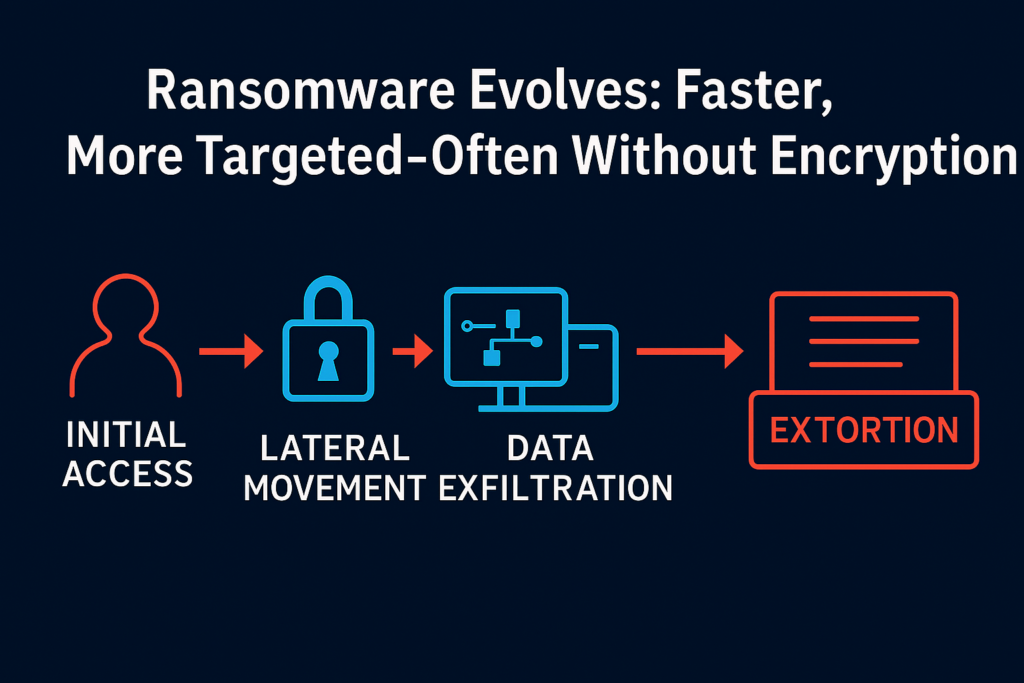
3) Ransomware Evolves: Faster, More Targeted—Often Without Encryption
Late‑2025 saw record activity heading into 2026. Even as gang brands churn, throughput rises—more victims, faster extortion, and increased “exfiltration‑only” cases (no encryption).
Manufacturing, technology, and retail are among the most impacted, with SMBs disproportionately represented.
GuidePoint GRIT 2026,
Broadcom/Symantec Ransomware 2026,
TechRepublic on DBIR 2025.
Containment mindset
- Pre‑incident: immutable/offline backups; segmented storage; egress anomaly detection for exfil.
- During: isolate identity systems; invoke clean‑room recovery; communicate fast & consistently.
- After: rotate secrets; rebuild golden images; tighten JIT access.

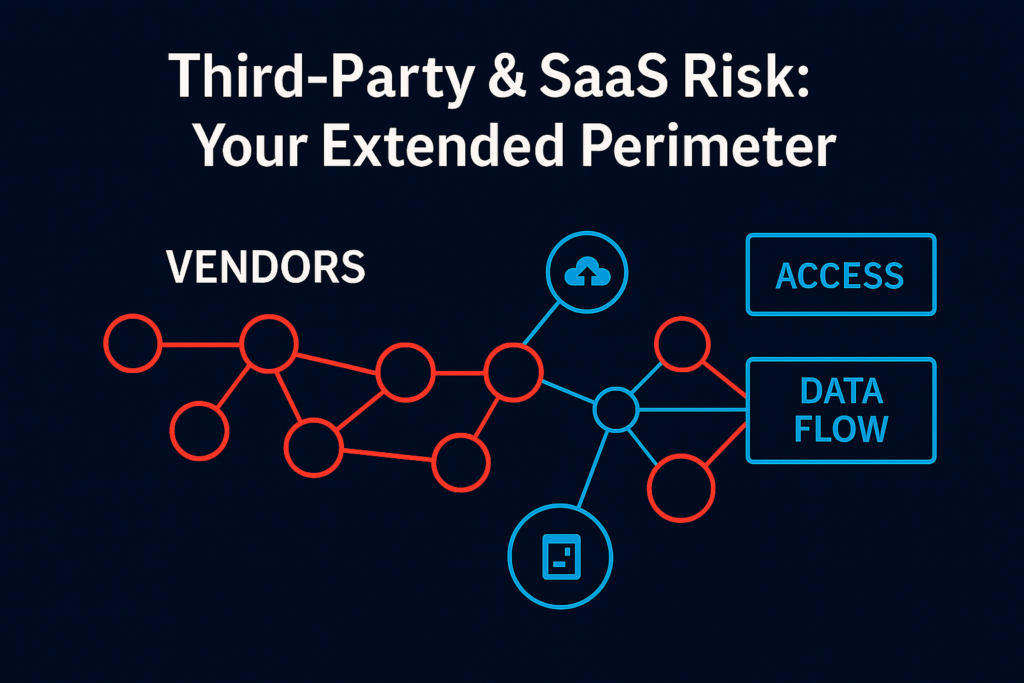
4) Third‑Party & SaaS Risk: Your Extended Perimeter
Verizon’s DBIR shows third‑party involvement doubled to ~30% of breaches, while exploitation of vulnerabilities surged—particularly at the edge (VPNs, gateways) where patching lagged (median 32 days; only 54% fully remediated).
In the EU, ENISA continues to highlight ransomware’s impact and rapid vulnerability weaponization across sectors.
Verizon DBIR 2025,
ENISA Threat Landscape 2025.
Actions
- Tier your vendors; enforce least‑privilege, isolated access and a kill‑switch to disconnect fast.
- Contract for continuous control monitoring and strict incident‑notice windows.

Vendors, cloud apps, and SaaS integrations expand the attack surface—making third‑party security a critical part of your 2026 cyber defense strategy.”
5) From Prevention to Resilience: Metrics Boards Track
2026 is the year cyber success is measured in TTD/TTC/TTR—time to detect, contain, recover. Boards want proof you can take a punch and keep operating.
IBM reports the global average breach cost dropped to $4.44M (AI‑aided response), while the U.S. average rose to $10.22M. Focus on recovery engineering, cross‑functional tabletops, and vendor dependencies.
SecurityWeek: Resilience 2026,
IBM 2025.
2026 Cyber Checklist (save & execute)
- Enforce phishing‑resistant MFA for staff, vendors, and admins. SecurityWeek
- Discover & govern AI: inventory LLM apps/agents, rein in shadow AI, set access controls. IBM
- Accelerate edge/VPN patching: aim for < 7 days on perimeter CVEs. DBIR
- Microsegment crown‑jewel apps; default‑deny east‑west. Illumio
- Detect data exfiltration (DNS/HTTP anomalies; cloud egress). Cobalt stats
- Immutable + offline backups; quarterly restore drills with timed RTOs. SecurityWeek
- JIT admin & session recording; rotate secrets post‑incident. SecurityWeek
- Vendor kill‑switch & contractual breach‑notice windows. DBIR
- Email/collab hardening (DMARC, link‑preview controls). DBIR
- Document a clean‑room recovery plan (gold images, identity rebuild). SecurityWeek
- Start post‑quantum crypto agility (inventory, pilot hybrids). SecurityWeek
- Make resilience KPIs board‑level (TTD/TTC/TTR, tabletop cadence, vendor exposure). SecurityWeek
Case Study: A Major Manufacturer’s Ransomware Disruption (2025) and the Resilience Lessons
In late 2025, Jaguar Land Rover (JLR) suffered a cyberattack that disrupted production and later correlated with sales impact—and was widely covered as one of the most expensive UK security incidents of the year.
Investigations and reporting linked the event to vulnerabilities in third‑party software and highlighted deep operational disruption.
International Compliance Association,
SecurityWeek (roundup).
What went wrong (public takeaways)
- Third‑party/ERP exposure can cascade into plant operations, not just IT systems. Lesson: treat vendor platforms as part of your own perimeter.
- Identity & availability coupling: when AD/SSO and production scheduling collide, downtime multiplies. Lesson: plan for identity isolation and degraded‑mode ops.
What to implement now (you don’t need to be JLR‑sized)
- Vendor Kill‑Switch Drills: practice disconnecting a critical SaaS/ERP and running in “manual” or reduced‑function mode (pre‑defined SOPs).
- Identity Safe Mode: a hardened, out‑of‑band identity instance for recovery (minimal accounts, offline backups, signed change process).
- Work‑cell Segmentation: microsegment production cells and gateways; least‑privilege service accounts; monitor east‑west traffic.
- Exfil Detection: baseline and alert on unusual egress destinations and volumes from key plants and data stores.
Why this matters: Verizon’s DBIR shows third‑party involvement has doubled, and edge devices are an accelerating vector. If you can operate in degraded mode and restore identity cleanly,
you’ve converted a business crisis into an ops incident.
DBIR 2025.
Who Else Covers Cyber Well—and How You Beat Them
- Dark Reading—fast on zero‑days and strategic outlooks. See 2026 predictions. Beat them with checklists and sector‑specific runbooks (SMB/manufacturing).
- The Hacker News—high‑tempo threat briefs and weekly roundups. Example weekly. Beat them by adding “change by Friday” action items.
- Krebs on Security—investigative reads with real impact. KrebsOnSecurity. Beat them by pairing investigation links with your exec‑friendly summaries.
- ENISA—authoritative EU data and trends. ENISA ETL 2025. Beat them via practical EU‑SME action maps (NIS2‑ready content—add in a follow‑up post).
References & Sources
- Google Cloud — Cybersecurity Forecast 2026; ISACA — 6 Cybersecurity Trends Shaping 2026; Dark Reading — 2026 Predictions
- Mandiant/Google Cloud — M‑Trends 2025; ISACA — 2026 Trends
- Broadcom/Symantec — Ransomware 2026 (White Paper); GuidePoint GRIT 2026 — Record Ransomware
- Verizon — Data Breach Investigations Report 2025; TechRepublic DBIR 2025 summary
- ENISA — Threat Landscape 2025
- SecurityWeek — Cyber Risk Trends for 2026; IBM — Cost of a Data Breach 2025
- International Compliance Association — Top 10 Breaches of 2025; SecurityWeek roundup — JLR aftermath & other items
Free: 2026 Cyber Resilience Scorecard (Template)
Want a one‑page scorecard with TTD/TTC/TTR targets, vendor kill‑switch checks, and recovery drills? Contact us and we’ll send the template.






One Comment